Security¶
Important
Demo Range Access - User Account Site
- Open web browser (FIREFOX preferred from OpStations)
- Navigate to 10.50.X.X/classinfo.html ← Instructor will supply last octets→
INPUT YOUR USERNAME ONLY, STORE OUTPUT IN YOUR NOTES, RESULTS WILL BE DELETED
Building Op Stations¶
- Login to CVTE environment
- Open Google Chrome Web browser
- Click next to go into ccoecaas.net
- Read and agree to user agreement
- Access Aira Automation CSTN Production ( should automatically place students in )
- Select to Catalog option on left side menu
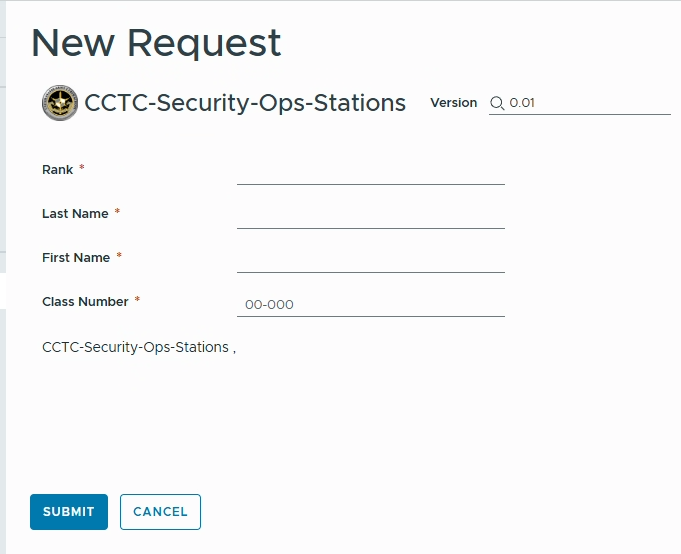
- Select CCTC-Security-Ops-Stations (request)
- Fill in fields on New request page and hit SUBMIT
- Your Ops Station Deployment will start building. Should take about 5-10 minutes to complete
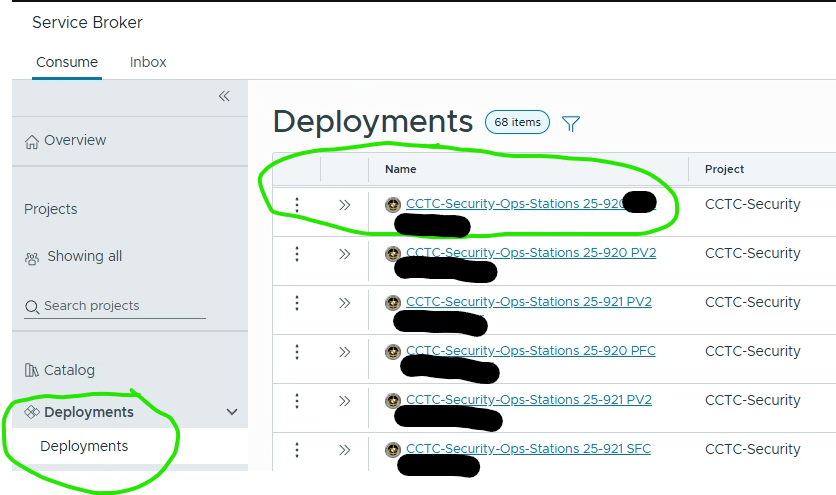
- Select Deployments on left side menu
- Select your build to view both Linux and Windows Op Systems
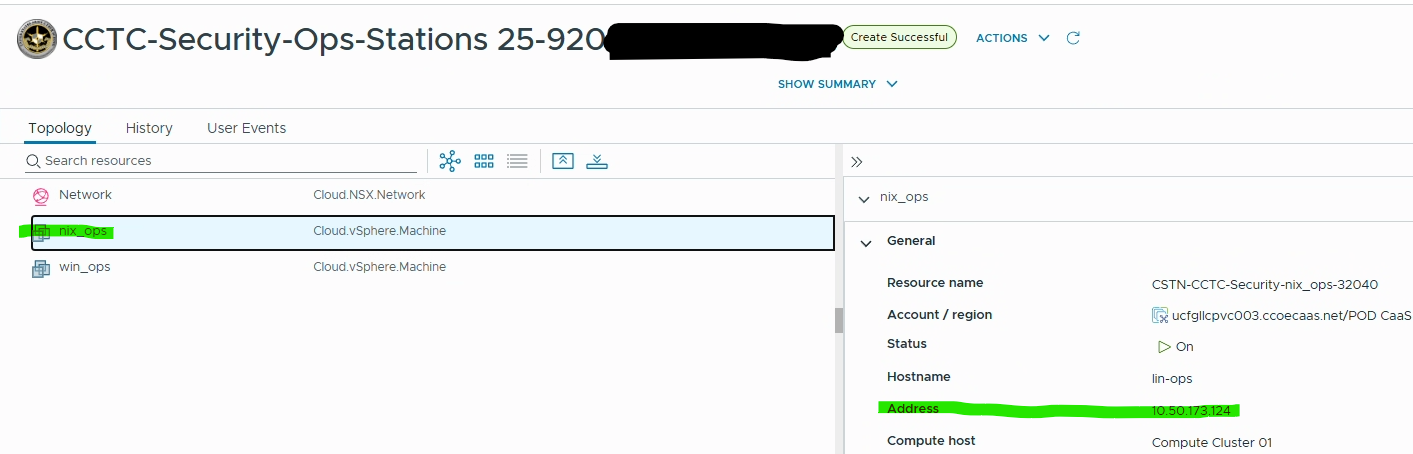
- Select either VM from your Deployment to view systems IP address on the right side window
Note
You can and should RDP into these Op Systems from your CVTE client systems. RDP will allow for cpy/pst and a smoother user experience.
Important
The CTFd Servers can only be accessed via Op Stations ( Lin or Win )
The Vision for Security and Exploitation¶
The Security module is based on the principle of understanding the basis of exploitation. Deep understanding of how systems and exploitation really work allow for advanced offensive and defensive operations. Because of this, exploitation is the main thing that is taught. On the surface, this may appear to only teach offensive tehniques. However, the students are then asked to research mitigation techniques. For example, if you understand why pickles are dangerous in a Python application, you can easily search for the dangerous use of pickles and mitigate by developing a safe method to do the same thing.
As an example to the above, find the vulnerability:
conn,addr = self.receiver_socket.accept()
data = conn.recv(1024)
return cPickle.loads(data)
If you don't understand how pickles and pickle exploitation work, you may not be able to identify it. Essentially, this code unpickles arbitrary data that it recieves. How would you mitigate this without understanding exploitation? You couldn't. But now that you understand what the danger is at a high level, you can create defensive mitigations. One way to protect this simple code is to verify data received with cryptographic signatures:
conn,addr = self.receiver_socket.accept()
data = conn.recv(1024)
recvd_digest, pickled_data = data.split(' ')
new_digest = hmac.new('shared-key', pickled_data, hashlib.sha1).hexdigest()
if recvd_digest != new_digest:
print 'Integrity check failed'
else:
unpickled_data = pickle.loads(pickled_data)
Reverse engineering is the fundamental skill under all exploit development and bug hunting. Therefore, it is the fundamental task used to attack and defend any and all systems. When you think of reverse engineering, do not associate it only with breaking C programs. Reverse engineering encompasses not only the aforementioned software analysis, but also systems analysis, protocol analysis, and hardware analysis.
For example, if you want to remotely control a Honda Civic, you need to find a remote exploit. This means that you need to reverse engineer multiple systems within the car. Most likely, the cellular data hotspot used for WiFi is run directly in the kernel that controls the entire car. Considering that this is a networked device running directly in the kernel, you can imagine that this is a good candidate for intial access and complete control of the car. As you continue reverse engineering the car, you will begin to understand how CAN works. It operates like a multicast protocol in that it sends all transmissions everywhere in the system. Imagining a rogue CAN device interupting communication on the wire is not difficult.
Likewise, if you do these things before a bad guy does, you can create mitigations specifically designed to mitigate those possibilities. For the above, a sensible person would not run the cellular hotspot in the kernel. In fact, they would keep it as far away as possible. Prevention of a rogue CAN device may require that CAN wires are not physically accessible except under maintenance conditions that are not trivial to fake, or take too long of a time to meet than would be realistically operable under as an adversary.
Security and Exploitation teaches the deep understanding of systems and their exploitation to create cyber actors that understand how to use and create offensive capabilities and defensive mitigations.